VPNs: not just sponsors of YouTube tech videos! If you think of Virtual Private Networks (VPNs) as data privacy tools or a way to access geographically restricted content, then the idea they’re dying out probably seems far-fetched. But if we’re talking about internet-based VPNs, the kind that enables access to corporate networks, there’s been plenty of prognostication that the last days of VPN may be upon us.
However, it’s also true that the landscape is changing. Modern network technologies like SD-WAN, SASE, ZTNA, and a variety of cloud solutions come with the promise of addressing many of the shortcomings of a VPN. VPNs aren’t as flexible as alternatives like SD-WAN, or as granular as zero-trust network access (ZTNA). Large-scale cloud computing, bring your own device (BYOD), and remote work also make for a WAN environment that’s more dynamic than traditional VPN. So today, sticking with VPN to support these situations means your IT teams are making some sub-optimal performance, security, and network visibility tradeoffs.
Back to the question at hand: Is it time to move on from VPN? For an enterprise-wide greenfield deployment or network refresh? Sure, consider modern VPN alternatives first. For networks that depend on VPNs today? It might not be worth the effort to lift and shift. Similarly, VPN might be “good enough” for your secure WAN connectivity, as well as considerably cheaper.
Here, to help you sort through the vagaries of “it depends”, let’s take a closer look at the state of VPNs in 2022, the problems they solve, the challenges they create, and some popular VPN alternatives for organizations.
Quick Note: What do we mean by VPN?
Depending on who you ask, the term “VPN” can mean a few different things. MPLS vs. VPN was a hot debate in the 2000s and 2010s. SD-WAN is a VPN alternative, but technically SD-WAN solutions often create multiple tunneled connections that are — oversimplifying here — site-to-site VPN connections.
So, what do we mean by VPN? Hardware or software appliances that use encrypted tunnels over the public internet to facilitate site-to-site connections or remote access for an organization. VPNs that use PPTP, L2TP, SSTP, IPsec IKEv2, and OpenVPN are common examples of how organizations implement the internet-based VPN we’re talking about here. For a deeper dive on different VPNs, check out our article on 6 top VPN protocols (and when to use them).
Are VPNs still relevant or are VPN alternatives the way to go?
In a word: yes. It’s clear VPNs aren’t dead or declining, and probably won’t be anytime soon. Unsurprisingly, VPN usage saw a pretty steep increase after the COVID-19 pandemic hit.

Many users today depend on VPN connections using solutions like Cisco AnyConnect, Pulse Connect Secure, and FortiClient VPN solutions to access enterprise networks. Similarly, many WAN locations still use firewalls, routers, and unified threat management (UTM) appliances to enable site-to-site connectivity via VPN tunnels.
What made VPNs so successful?
The short answer? Cheap enough, and fast enough. Traditionally, VPNs provided organizations an affordable way to enable “secure” access between sites and connectivity for remote workers through the public internet. Public internet bandwidth is much cheaper than leasing dedicated MPLS lines (you’ve probably heard of a T1 line). And for most companies’ needs, public internet performance is good enough. Those two points alone explain a large chunk of why VPNs became a staple of WAN connectivity for so long.
More recently, VPNs have been a quick, albeit imperfect way, to quickly ramp up work-from-home plans quickly. If you already had VPN appliances configured, adding more licenses and bandwidth was a quick way to ensure business continuity.
What are some of the challenges with VPNs?
VPN is far from perfect. There are plenty of challenges that make VPN the wrong solution for a lot of situations:
- Network performance. VPN tunneling inherently chews through more bandwidth than connections without tunnels. But on modern networks, that overhead isn’t an issue. The bigger performance impact comes from things like jitter, latency, and packet loss over the public internet, VPN appliances creating bottlenecks, and lack of support for services like QoS and dynamic path selection.
- Scalability. Site-to-site connectivity with an internet-based VPN can work well for a few locations that are relatively close geographically. Similarly, remote-access VPNs can serve the purpose of enabling small-to-medium scale remote work. However, as you layer in more sites, more remote workers, and cloud workloads, scalability becomes a challenge from complexity and a performance standpoint.
- BYOD support. While the client software has gotten better in recent years, it’s still not easy to support BYOD devices on a traditional VPN. The session-based nature of a VPN connection isn’t exactly a great fit for mobile devices that may jump from 4G to 5G to WiFi to airplane mode throughout the day.
- Security. While VPNs are “secure” in the sense they use strong encryption to transmit data, they have several security shortcomings. Traditional VPNs are effectively a form of castle-and-moat-style security that won’t do much in the way of traffic inspection, cloud security, or access policies.
- Complexity. Split tunneling, WAN optimizers, and additional security appliances all add up to more complexity. The network becomes more difficult to maintain.
When VPN alternatives solve many of these problems more elegantly and allow IT to focus on other tasks, those solutions get harder to justify as the right business decision.
VPN Alternatives: The Challengers
We’ve established that VPN isn’t the modern ideal for a lot of use cases, but that only really matters if VPN alternatives provide a better solution. Let’s take a look at some of the newer technologies that are taking VPN’s place, and the advantages they offer.
The cloud
I realize “the cloud” is a bit broad, but hear me out: Cloud computing has shifted network parameters significantly. Today, many business apps reside in the cloud instead of a corporate data center or branch office. Instead of using a VPN and traditional security appliances, organizations can leverage cloud apps coupled with solutions like single sign-on (SSO), identity-aware proxies, and cloud access security brokers (CASB) to meet business requirements.
ZTNA and SDP
ZTNA and software-defined perimeter (SDP) solutions create a logical perimeter around a network and enforce security policies based on user identities. This allows for a more flexible, cloud-friendly, and granular approach to secure network access than a VPN does.
SD-WAN
SD-WAN provides more flexibility and scalability than traditional internet-based VPNs. Using SD-WAN, IT gets features like QoS and dynamic path selection built-in. Additionally, an SD-WAN overlay aggregates multiple underlying transport mediums (xDSL, MPLS, 5G, etc) and reduces a lot of network and failover complexity. Further, SD-WANs that includes a network of PoPs can eliminate many of the latency and jitter problems associated with the public internet.
SASE
Secure Access Service Edge (SASE) integrates multiple networking and security functions (including ZTNA/SDP and SD-WAN) into a single platform. With SASE, which inherently has a cloud focus, the industry is pushing towards a convergence of networking and security in a single platform. If SASE can deliver on its promise, it can help IT reduce tool sprawl and complexity.
Auvik Helps IT Support VPNs
To review: Despite all the new options available to IT teams today, VPNs are sticking around for some time. In some cases, VPN is the “best” tool for the job. In others, it’s because IT has to support a legacy technology stack for a while.
Whatever scenario you find yourself in, there’s a good chance Auvik can improve your overall network visibility, and make it easier to troubleshoot VPN issues.
Auvik makes it easier to support VPNs in a lot of ways, including:
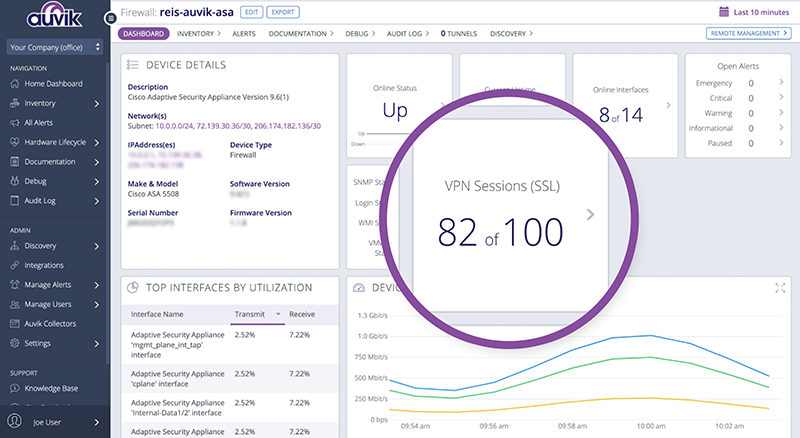
- At a glance tunnel dashboards. The Auvik tunnels dashboard makes it easy to monitor site-to-site VPN IPsec tunnels.
- Track VPN Sessions monitoring. Track active VPN sessions on select firewall dashboards for Cisco ASA, SonicWall TZ, and SonicWall NSA devices.
- Verify network traffic. If users are using the network for reasons other than legitimate business purposes, that can unnecessarily put sensitive data at risk. Auvik TrafficInsights provides deep visibility into the traffic traversing a network so you can address these risks.
For more on how Auvik helps IT support VPNs, check out VPN Monitoring: Keeping Remote Workers Connected With Auvik.
Your Guide to Selling Managed Network Services
Get templates for network assessment reports, presentations, pricing & more—designed just for MSPs.