Software-defined WAN (SD-WAN) is a software overlay that decouples WAN configuration and management from the underlying network transport medium (5G/LTE, MPLS, xDSL, etc) and dynamically routes WAN traffic.
To the uninitiated, that’s a mouthful. But it’s one of the most interesting trends of the last few years. Let’s jump on the bandwagon!
Time for a primer on SD-WAN, why it matters, and where it’s heading now and into the future.
Quick sidebar on SDN
To understand SD-WAN, you need to understand the broader concept of software-defined networking (SDN) first. SDN is a form of network virtualization that moves the network control plane (the functions that decide the how and why of data transport) away from the physical devices themselves, to an independent software controller. Those devices are now strictly concerned with the data plane (the actual moving of the data to and from its destination).
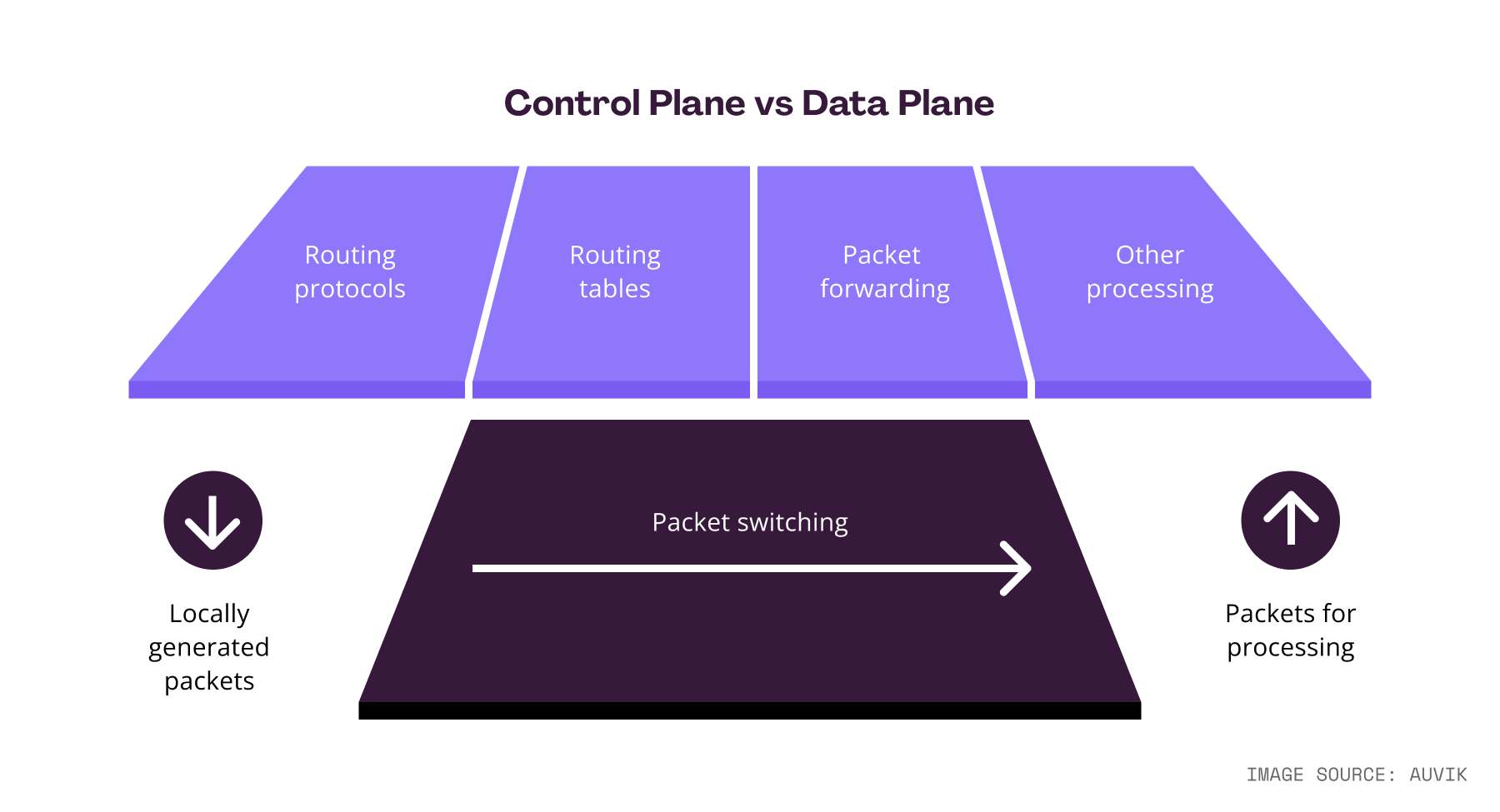
Instead of all your networked devices running separate instructions and acting autonomously, and constantly trying to maintain connectivity, they are all directed by one software-based central controller.
While SDN often refers to LAN connectivity in virtual data centers, the same concepts apply to WAN connectivity.
SD-WAN, explained
Think of SD-WAN as a specific expression of SDN. Instead of needing to provision individual routers using something like SSH, a serial connection, or SNMP, the configuration for all your routing hardware is centralized in a software-based controller. The result is a WAN topology where the underlying transports (5G/LTE, MPLS, xDSL, etc.) are essentially unimportant because the SD-WAN overlay can dynamically route traffic across any of them.
This software-based topology has a lot of advantages, like reducing costs, increasing network resilience, and simplifying WAN management.
Unfortunately, a lot of the popular talk around “what’s SD-WAN?” is often heavy on marketing. And on the other end of the spectrum, as you can see so far, the technical information out there isn’t exactly light reading. Here, we’ll strike a balance between technical and beginner-friendly that unpacks it for network pros.
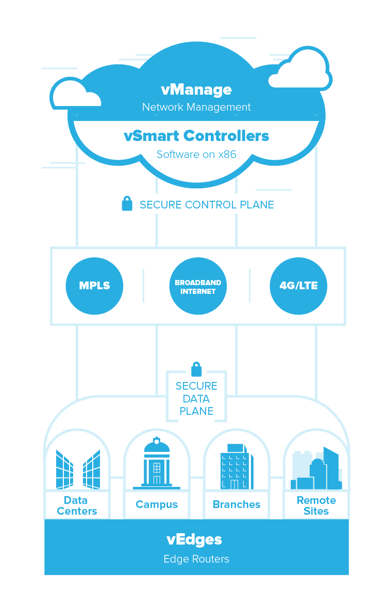
What are the main components of SD-WAN architecture?
It’s not exactly a unified language, so we’re boiling down concepts and terminology from vendors and the MEF reference Wiki to something concise. SD-WAN architecture consists of these main components:
- SD-WAN Edges. These are the connections between service provider networks and your WAN endpoint locations (e.g. campuses, branch offices, or corporate data centers). The appliances making the connections can be physical or virtual. The “overlay” is created by connecting these edges together using encrypted tunnels.
- Underlying WAN transports. These are the hardware transport mediums we’re all familiar with: xDSL, MPLS, and 5G/LTE.
- SD-WAN controller. The component that manages the edge connections. A controller takes care of the “control plane” tasks mentioned above: IP address management, routing policy configuration, and device management.
- SD-WAN orchestrator. The component that manages functions like performance, analytics, usage, and policy configuration. Often, orchestrator and controller functions are combined in a single solution.
What are some common features?
SD-WAN solutions provide a variety of routing and network optimization features, including:
- QoS. Most solutions offer a variety of QoS functions, like traffic shaping, to help reduce latency, jitter, and packet loss. Features like Cisco’s application-aware routing allow administrators to set SLAs to optimize performance for specific business-critical apps.
- Support for multiple transports. SD-WAN edges can terminate a variety of WAN transports, increasing network flexibility and opening up a variety of failover options.
- Dynamic path selection. The overlay automatically selects the optimal inbound and outbound data paths via dynamic path selection. It will continuously monitor link performance and updates path selection on the fly.
- Simple management. Simplicity is actually one of the core tenants of SD-WAN management. According to Gartner, the expertise needed to configure it should be comparable to that of home networking equipment.
- Service chaining. With service chaining, additional network and security functions like firewalling and IPS/IDS can be layered into the topology.
- Link aggregation and load balancing. SD-WAN allows administrators to aggregate links and balance loads across them to improve network performance.
Different types
There are multiple approaches to SD-WAN architecture. While vendor-specific implementations are still a little wild west, they can be loosely grouped into 3 categories:
- Appliance-based. A virtual or physical appliance at each edge location creates the overlay. Appliance-based solutions can be implemented by individual organizations or provided by a service provider. In some cases, telcos that used to sell MPLS services now also offer managed SD-WAN services.
- Cloud-based. Similar to appliance-based SD-WANs, but adds a centralized cloud-management interface, and often includes optimized routing for specific cloud vendors.
- SD-WAN with a network of PoPs. Some providers include a private network backbone along with cloud-based SD-WAN. The reasoning being the private network of PoPs (points of presence) should deliver robust middle-mile connectivity, similar to MPLS, to improve performance and reliability where public Internet connections are highly variable. Often, these private backbones include performance SLAs comparable to (or better than) MPLS SLAs.
What’s so great about SD-WAN, anyway?
We’ve covered the what, but that doesn’t answer why for your networks. For many organizations, SD-WAN benefits are usually more than one of these:
- Better performance for distributed networking. Modern networks are more dynamic and distributed than ever. Endpoints reside in the cloud, home offices, branch locations, and corporate data centers. Mobile work makes things even more complex. SD-WAN does a much better job accommodating these use cases than traditional solutions like Internet-based VPN or MPLS. Dynamic path selection and WAN optimization features can further improve overall network performance with SD-WAN.
- Streamline IT ops and network optimization. SD-WAN does for WAN routing what server virtualization did for server administration. By adding a software layer to WAN configurations, it enables network automation and streamlined IT ops by adding a software layer to WAN configurations.
- Secure WAN connectivity. While note strictly a security solution (though edge connections usually employ encrypted tunnels), many modern solutions couple SD-WAN routing with features like anti-malware, URL filtering, IPS/IDS, and zero trust network access.
- Reduced costs. Reduced costs of bandwidth (expensive MPLS vs cheap public Internet) are an obvious bottom-line benefit. However, because it helps streamline and automate operations, SD-WAN can also significantly reduce IT’s operational costs. Further, IT can reduce appliance sprawl and spend on proprietary network and security devices.
- Increased network resilience. IT teams can leverage multiple underlying network transport modes in active-active or active-passive failover modes. If a fiber link from one ISP goes down, they can fail over to another fiber link, an MPLS line, a satellite connection, 5G, or any other WAN transport method.
Of course, no technology is without tradeoffs, and SD-WAN isn’t right for every solution. For simple site-to-site connectivity, Internet VPNs are often still the simplest and most practical option for simple site-to-site connectivity. In other cases, the incremental improvements SD-WAN can bring simply don’t justify the migration cost and complexity.
Additionally, while SD-WANs with a private network backbone can have performance and operational advantages, the costs add up. And if you’re just replacing something like MPLS with SD-WAN based on the public Internet, you lose out on the telco SLAs.
WAN networks compared
SD-WAN vs traditional WAN
Abstraction is the fundamental difference between traditional router-based WAN and SD-WAN. But, if you’re not familiar with SDN already, that answer is a bit… abstract.
Abstraction, in general, is the process of taking away or removing characteristics from something in order to reduce it to a set of essential characteristics. Like a very basic form of virtualization, it helps in reducing programming complexity and efforts.
What does that mean exactly? Let’s revisit the data plane and control plane concepts. On a traditional WAN, the data plane and control plane live on the same routing device (e.g., a router or firewall appliance). The device has a management interface administrators use to configure routing protocols. Based on how administrators configure this control plane, the device in turn follows those routes on the data plane. The big thing to remember here is that to configure an entire WAN, administrators must configure the control plane of each routing device.
With SD-WAN, administrators can now configure a single controller, and that configuration will propagate all the necessary routing information down to all the individual devices. That’s abstraction: The software layer abstracts the individual routing devices.
SD-WAN vs MPLS
To conceptualize why that WAN abstraction layer is useful, let’s compare traditional MPLS-based WAN connectivity with SD-WAN.
With MPLS, organizations connect branch offices and corporate networks using dedicated circuits leased from telecom providers. These circuits offer isolated, high-throughput connectivity between sites, but come with several challenges, specifically:
- MPLS bandwidth is expensive. MPLS bandwidth is still significantly more expensive than public Internet connections.
- MPLS isn’t cloud-friendly. A lot of modern WAN traffic goes from a branch location to a public cloud. Traditional MPLS isn’t designed with this use case in mind, and traffic is often backhauled for inspection before being sent on to the public internet. This can create a variety of latency and performance issues.
- MPLS takes time to provision. Standing up a new site with an MPLS circuit can take weeks.
With SD-WAN, on the other hand, organizations can create a WAN using whichever underlying transport mode best meets application requirements. That means MPLS can be replaced (or supplemented) with cheaper public Internet bandwidth. It also means that the time to stand up a new link can be greatly reduced, and traffic backhauling can be avoided altogether through application-aware routing.
Who are the major providers?
In recent years, acquisitions, product revisions, and updates have changed the landscape. Like several categories in networking, there’s no single dominant provider. However, it should come as no surprise that many of the names topping Auvik’s 2021 Network Vendor Diversity Report are also major SD-WAN solution providers.
At the start of 2022, the most popular SD-WAN vendors are:
- HPE Silver Peak
- VMware SASE SD-WAN
- Cisco Viptela SD-WAN
- Cisco SD-WAN Powered By Meraki
- Fortinet Secure SD-WAN
- PaloAlto Prisma SD-WAN
- Bigleaf SD-WAN
- Cato Networks SASE
- Aryaka Managed SD-WAN
- Oracle Talari SD-WAN appliances
Imagining the future of SD-WAN

Here’s three of the biggest trends for SD-WAN we think we’ll continue to hear more of soon:
- SD-WAN and working from home. Over the next few years, we can expect solutions like SD-WAN and SASE to increase in popularity for connecting individual users. Connecting remote workers via VPN is ok for use cases like email, but isn’t ideal for latency-sensitive or bandwidth-intensive apps. SD-WAN vendors are working to bring costs down to the point supporting “branch office of one” use cases (check out our podcast on the subject) are economically feasible for more enterprises.
- SASE. Pronounced “sassy”, it’s short for secure access service edge. We’re already seeing vendors that touted their platforms as “SD-WAN” market the same solutions as SASE, making it hard to differentiate the two. But SD-WAN is really just one component of SASE which combines SD-WAN and several other network functions into a single platform. The idea is to support the dynamic connectivity needs of modern IT, emphasizing zero-trust access.
- Next-generation SD-WAN. While there is some standardization around SASE thanks to MEF, next-generation SD-WAN current isn’t much more than marketing buzzwords. That said, expect to see some emerging trends around the use of ML and AI to further optimize and improve WAN connectivity (yay more buzzwords!).
SD-WAN evolved quickly throughout the last decade, and we expect more evolutions through the 2020s. Conditions around the modern work environment are also evolving, and we think it’s actually playing to SD-WAN’s strengths. We’re seeing a general trend towards converging networking and security functions, and an increased focus on supporting distributed IT use cases.
There’s no one-size-fits-all answer for network monitoring. Regardless of the implementation, it’s still essential for IT to monitor overall network performance. That requires a remote network management tool that can provide deep network visibility and real-time alerts. Auvik supports monitoring for over 15,000 devices from 700+ vendors, including devices from major SD-WAN providers.
Ready to see how Auvik can help optimize your existing network? Get your free 14-day Auvik trial here.
Your Guide to Selling Managed Network Services
Get templates for network assessment reports, presentations, pricing & more—designed just for MSPs.






You’re missing a great vendor – https://www.bigleaf.net/
We use them and are a fan!