As a network evolves over time, new network infrastructure devices are added, old devices begin to show their age, and some devices are completely forgotten about. It’s a natural consequence of mergers, upgrades, staff turnovers, and other common occurrences that contribute to redundancy or excess complexity in IT infrastructure.
Left unchecked, a network can become a complicated, unmanageable mishmash of network devices that are riddled with security vulnerabilities, place unnecessary demands on IT time, and bloat operating costs.
Fortunately, keeping IT infrastructure fresh and fit for purpose is easy. Here are five tips to help.
1. Maintain an up-to-date network inventory
One of the main causes of outdated network devices is a simple lack of information about what’s on the network. After years of mergers, staff turnover, and changes in IT support providers, chances are good that an organization will find itself with at least some hardware or software that’s been long forgotten in a literal or figurative dusty corner.
If older systems are known to exist but aren’t fully understood, the default response can be to keep everything around and online, out of fear that shutting something off will have negative, unpredictable consequences.
But just because it’s the default response doesn’t mean it’s the best response. In fact, if you know older systems and devices exist, it’s even more important to map the network and document the inventory you find, including where and how it’s connected to the network.
Thankfully, you don’t have to do this manually. Auvik can give you complete visibility into the devices connected to the network, including details like make and model, serial number, IP address, and the physical switchport the device is connected to. And since it’s a real-time map and inventory, Auvik will always be up to date, even when there are changes to the IT infrastructure.
2. Replace devices that are reaching end of life or are outside of warranty
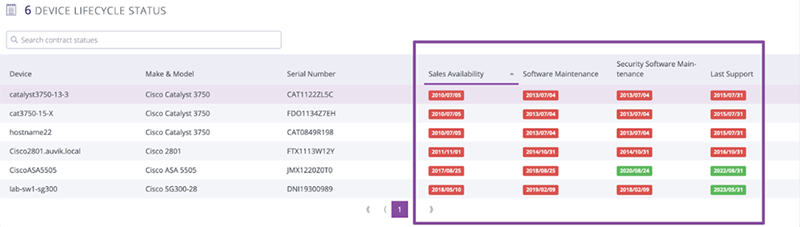
Once you have a complete inventory of network devices, it’s time to sort through the list to find devices that are approaching—or have already surpassed end-of-life, warranties, or support contracts.
Features like Auvik’s Cisco Service API can help streamline this process. For example, in Auvik, you can see whether Cisco network equipment is under a current or expiring support contract, if the device is eligible to receive critical security updates, and if the device is still available for purchase.
With a complete list of outdated network infrastructure devices, you can make the business case to replace them before they slowly but surely go kaput.
Replacing devices doesn’t have to be an immediate expense, either. You can maintain the list and estimate when other devices will have to be replaced. This inventory allows you to make the business case for device upgrades and to have hardware refreshes built into IT budgets for future quarters. And by proactively identifying devices and replacing them in bulk, you can get a better deal.
That’s what Jamie Warner, owner of Australian MSP eNerds, does. Each year, Jamie runs a three-month group buy campaign through Dell or HP to replace desktops and laptops that are more than four years old.
Through this process, the vendors sell more product than they usually do, the clients can rest easy knowing their equipment is regularly refreshed to keep pace with business demands, and Jamie makes between $250,000 to $350,000 in extra revenue in a single quarter.
3. Decommission and dispose of unnecessary devices
It’s often much harder (and less fun) to migrate and decommission an old device than it is to set up a new one. And if you’re looking to increase network capacity, it’s often easier to add devices such as switches and access points, rather than replacing existing infrastructure.
But following IT infrastructure best practices means that whenever you upgrade to a new system, you need to decommission the old one.
Once you’ve successfully decommissioned an old device, you can safely remove it from the network. To keep it from cluttering the workspace (and potentially being plugged back in by someone who stumbles upon it), dispose of the device by bringing it to a special recycling center or returning it to the manufacturer.
4. Keep an eye out for security vulnerabilities
For the remaining devices, it’s important to ensure they’re running on the latest software and firmware versions available.
If outdated versions are in use and bugs go unnoticed, it creates a huge security vulnerability in the network. Just look to the recent Cisco ASA firewall fiasco, where 12 firmware vulnerabilities could allow unauthenticated remote attackers to gain control of an ASA device.
Auvik automatically collects the current software and firmware version of every device it discovers, so you can quickly see which version it’s running. As network device vendors issue vulnerability warnings, you can easily identify devices that are at risk and update them to the most recent version, keeping the network healthy and secure.
5. Migrate to the cloud where possible
By now, most organizations have realized the benefits of moving some, most, or all of their business applications to the cloud. The cloud typically offers better security and performance, at a lower price, than housing resources on-premises.
As a bonus, by outsourcing services to the cloud, organizations can also make their on-premises operations much simpler and clutter-free. Migrating to the cloud also allows you to decommission the resources you’re replacing as you go.
But, remember, moving services into the cloud doesn’t necessarily mean all your assets are always fresh and up to date. You still need to ensure the office network—the critical asset all your users used to connect to the cloud—is always up-to-date and running in top shape.
Your Guide to Selling Managed Network Services
Get templates for network assessment reports, presentations, pricing & more—designed just for MSPs.