Today, 94% of enterprises use a cloud service in some capacity, and by 2020, 83% of entire enterprise workloads will be stored in the cloud. This presents a huge challenge: The network—and a strong internet connection—is now the lifeline to everything employees use and need to get things done. 100% uptime is now more than an expectation—it’s mandatory. To effectively take care of the networks you manage, keep users connected, and keep everything secure, you need to know two things: How the network is performing, and how the network is being used. That’s where Auvik TrafficInsights comes in.
Auvik has always been great at showing you the first. With real-time network mapping, inventory updates, and customizable alerts, you’ll have an accurate picture of the network and you’ll know when something’s wrong.
With the launch of TrafficInsights earlier this year, we’re now also great at showing you the second. TrafficInsights helps you see what’s travelling through the network so you can spot irregularities and ensure the network is being used properly.
What is Auvik TrafficInsights?
TrafficInsights is Auvik’s traffic analytics feature. Using machine learning, TrafficInsights complements flow data with additional metadata—like source and destination geography—so you can really understand the traffic, even if it’s encrypted. (NetFlow v5 and v9, IPFIX, sFlow, and J-Flow are all supported.)
With TrafficInsights, if any network traffic flows through a flow-enabled network device, you can see who’s on the network, what they’re doing, and where their traffic is going.
So let’s investigate some common network cases you or your techs face day to day—and how TrafficInsights can help:
Case #1: You get an alert that the network is at peak utilization
Before TrafficInsights, identifying the reason why your client’s internet bandwidth was maxed out was a guessing game.
You knew how much bandwidth was being used, but you didn’t know what the traffic was or if it was legitimate.
In TrafficInsights, however, all traffic reports are broken down by application group and application. The Application view lets you choose the different groups of applications or choose specific applications you want to see.
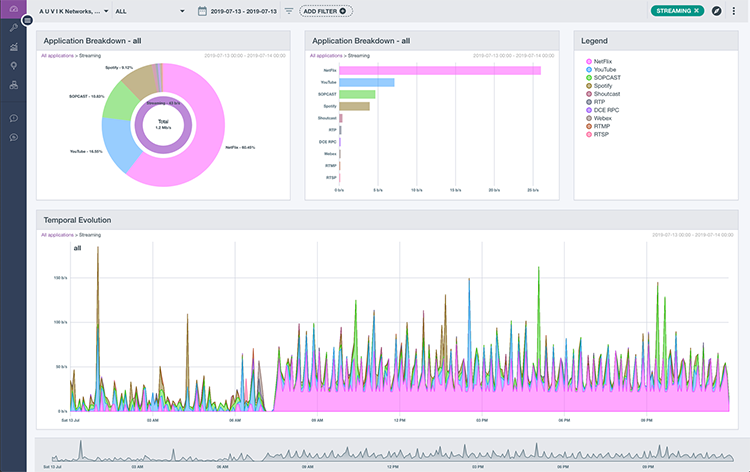
That means you’re able to determine if the traffic is legitimate, or if it’s someone streaming The Office (which is what’s likely happening in the screenshot above). If bandwidth is being spent on a personal app, you can drop into the endpoint causing the spike and shut it down or work with the end user to stop it.
If the network is reaching peak utilization because of legitimate business traffic, then you can make the case for your client to invest in a better internet connection. It’s a capacity planning dream come true.
Case #2: The network grinds to a halt at noon
Network performance issues can arise at the most inconvenient times—like when you’re driving to pick up lunch at noon.
Since most tools require you to catch the issue in real-time, that means you’d be skipping lunch… again.
That’s not the case with TrafficInsights. Since TrafficInsights stores flow data for 14 days, you don’t have to hop on your computer immediately—you can go back in time to investigate an issue.
Using the time interval selector at the bottom of the TrafficInsights dashboard, you can select a specific time frame within a specified date range—like Tuesday from noon to 1 p.m., for example.
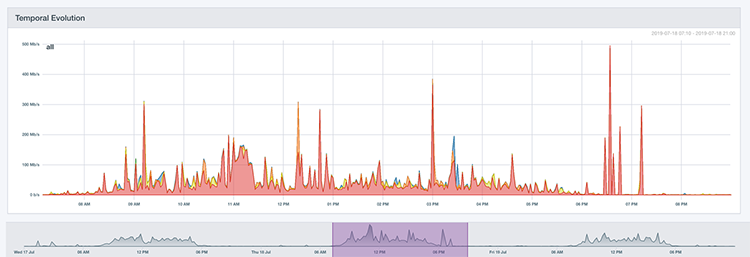
Your time frame selection is maintained as you switch dashboard panels, you’re able to dive into IP details and application usage as part of your investigation.
Using the Top Talkers view, you can see exactly which device is using up all the bandwidth during your time range, and you can trace it back to the specific user of the device:
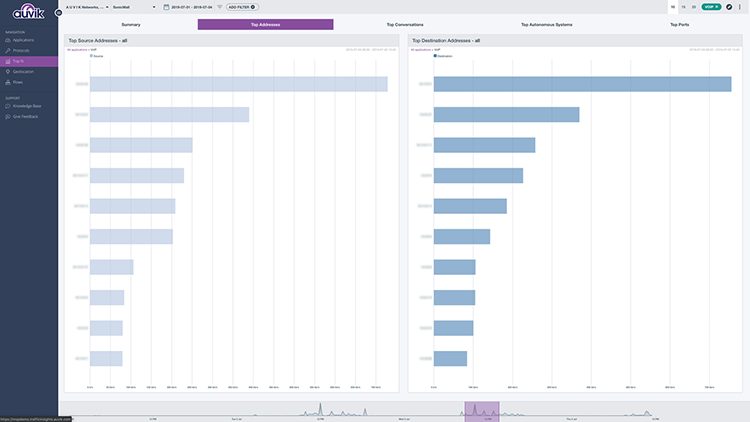
To see why the user is taking up so much bandwidth, you can navigate to the Applications breakdown and determine if they’re backing up files while away from their desk or if they’re streaming Netflix while they eat their lunch.
Case #3: Certain countries are off-limits
You may manage networks in a highly regulated industry where communication with certain countries isn’t allowed. But how can you know when data is passing through a destination it’s not supposed to be in?
With TrafficInsights, it’s as easy as looking on a map. The Geolocation area in TrafficInsights shows you the distribution of traffic by geographic location:
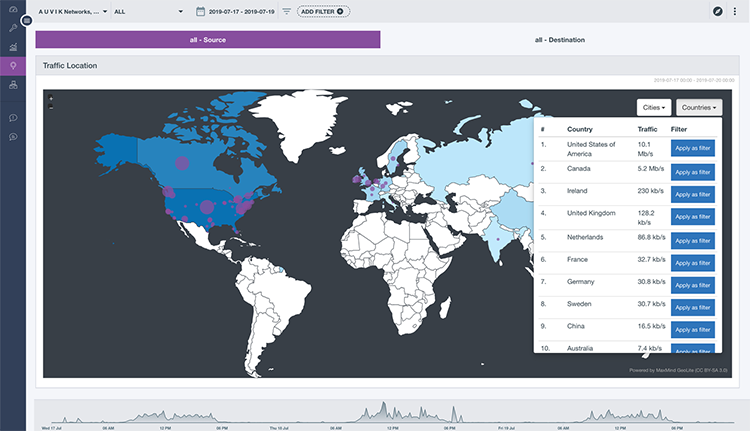
In this view, you can see the source and destination IP addresses of all the network traffic. This allows you to easily spot traffic bound for sanctioned countries you or your client have no business dealings in, identify which device is sending the traffic, and isolate the device the traffic is coming from.
If you determine the traffic is illegitimate, potentially malicious, or headed to a sanctioned country, then you can take action and add restrictions to stop it in its tracks.
And just like that, you’ve quickly gotten to the bottom of three common cases—and you look like the Sherlock Holmes of network management.
Ready to see more of TrafficInsights?
To test Auvik’s remote management features for yourself, sign up for a free 14-day trial and get full access to your network from the comfort of your desk.
Your Guide to Selling Managed Network Services
Get templates for network assessment reports, presentations, pricing & more—designed just for MSPs.