My guest today is Wes Spencer, Chief Information Security Officer at Perch Security. He’s a frequent speaker and advisor to companies big and small on cybersecurity, and he currently serves on the Department of Homeland Security AIS advisory committee—that’s the Automated Indicator Sharing committee.
Wes and I will be talking about the recent surge in cyberattacks targeting MSPs, what they mean for the industry, and importantly how to protect yourself and your clients.
Before we get there, I wanted to give a quick shout to everyone who completed our listener survey in August. I got some great feedback and ideas, which I’ll be incorporating into the show—starting with this episode. A bunch of you asked for more episodes on security topics so that’s why Wes Spencer is here today, and there will be more security and protection topics in future episodes as well.
Listen here
Couple of other comments from the survey that I wanted to quickly address.
One listener asked me to specify which episodes are audio and which ones are audio-video. All of the Frankly MSP episodes are audio only. We were posting the audio tracks to YouTube with a static image, which may be what has caused the confusion, but we’ve stopped doing that. So the best place to hear the show is either on the Auvik website through the embedded player or through your choice of podcast app. We’re on pretty much every major player, including Apple Podcasts, Google Podcasts, and Spotify, plus most of the smaller ones as well like Pocket Casts, Overcast, Castbox, and Stitcher. Listener’s choice.
Another listener requested written bullet points of what’s in each episode along with timestamps so they can see where in the episode each point is discussed. This is exactly what the show notes for each episode contain—a time-stamped outline of all the content—plus links to any additional content that’s mentioned such as articles, books, and interviewee contact information. And every once in a while, there’s some cool bonus content, like a rap puppet video.
I’ve started adding the link to the show notes in the episode descriptions when I publish the episode, which should make it easier to click through right from your podcast app.
All right, let’s dive into the conversation with Wes Spencer of Perch Security about MSP-targeted ransomware attacks.
What You Can Do About MSP-Targeted Ransomware: Interview With Wes Spencer

[03:44] MSPs are being targeted by cyber criminals. Wes has seen at least a dozen focused systemic ransomware attacks in the last 30 days.
[04:28] One of the challenges that Wes has been experiencing is that cyber criminals use anonymity in every way including using cryptocurrency for payments.
[05:03] Sodin is one of the attacks that Wes and his team has been seeing lately. These attacks are from three very specific cyber threat actors.
[05:59] Wes has been tracking threat actors for years. He made a documentary about the takedown of the Silk Road. The GandCrab campaign is similar in the way that they are bragging about their success.
[06:40] Many GandCrab threat actors did make millions.
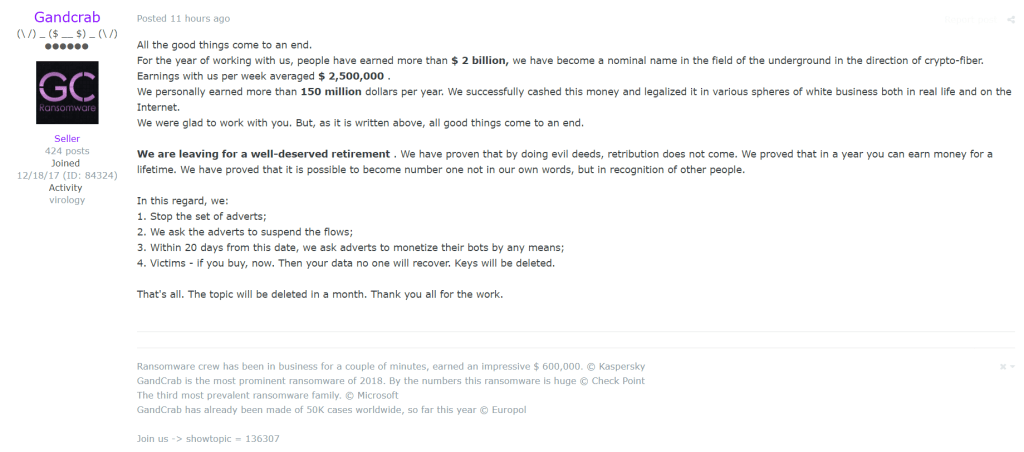
[06:54] In many ways, the bad guys are winning, because they’re going after industries that aren’t fully prepared. They’re also operating in foreign countries where there isn’t extradition. They’re also three or four steps ahead of most cybersecurity practitioners.
[07:26] Law enforcement agencies are still looking at GandCrab even though they are no longer active.
[08:14] Law enforcement is very interested in these cyberattacks. They’re trying to understand how many specific threat actors there are, what industries they’re going after, and what the attacks are looking like.
[08:48] Wes is seeing a number of MSP breaches specifically going after the RMM. Law enforcement is very interested in looking at the techniques they’re using to do this.
[09:16] Law enforcement is also interested in the actual money movement. Even though they’re using cryptocurrency, there are ways that the money movement can be tracked.
[10:02] The high volume of attacks makes it difficult for law enforcement to get involved in all of them. It’s frustrating for MSPs when they don’t have the resources to fight these attacks.
[11:25] Cyber threats are a huge concern for MSPs, and many are going through the ropes of tabletop testing, looking at their controls, and having discussions with vendors and partners.
[12:00] Wes is doing a free tabletop test session specifically for MSPs at IT Nation Connect at the end of October. It will simulate a real attack and lets participants see how they stack up against the attack.
[13:03] To lock things down, you have to use two-factor authentication. If one single employee doesn’t have two-factor enabled, you can get attacked.
[13:57] You also have to be aware of your risks like remote desktop protocol being hit by the internet. Turn RDP off and require a VPN to access the network.
[15:13] Know what your customers are doing and what type of risk they pose to you. Have some conversations and understand what their online processes look like.
[16:27] You might want to think about whether you’re willing to accept a client that doesn’t want your standard security package. You could make exceptions, but have them sign a waiver.
[17:15] When a client gets hit, they blame the MSP no matter who may be at fault.
[17:53] You also have to think about what things are critical for a client to have and how you will price it.
[18:07] MSPs need to understand what a real cybersecurity framework (CSF) looks like. Look at the cyber security framework from NIST.
[19:21] MSPs are the focus of attacks, because getting full access to the RMM gives the attacker full control over the MSP and all of their clients.
[19:41] The two attacks he’s seeing is just one client getting hit or the MSP getting hit. The latter is the vast majority of attacks.
[20:29] You need to understand your risk not just use tools. It’s also important to align yourself with the CSF and build a comprehensive security program. Be aware of how attacks happen.
[21:06] Attackers will spend a significant time in your network once it’s accessed.
[21:51] It takes the attacker time to learn your network. This gives the MSP time to detect and stop the attacker. It’s critical to have good visibility on your network.
[22:27] Don’t give up! MSPs can leverage the best practices of others that have gone before them. Take a risk-based approach. MSPs can and should work together to fight this common enemy.
Links from this episode
- Wes Spencer on LinkedIn
- Perch Security
- Department of Homeland Security AIS Advisory Committee
- The Silk Road: The Rise and Fall of the World’s Largest Online Black Market (video)
- NIST Cybersecurity Framework
- Cyber Security Framework ebook from Perch Security
- MSP subreddit
- IT Owners’ Compass Facebook group
- IT/MSP Entrepreneurs Facebook group)
- Frankly MSP Community
Listen here
Like what you hear? Listen and subscribe.


